What is shadow IT?
Most IT leaders and CIOs are no strangers to employees downloading their own apps for work, whether it's because they don't want to go through the approval processes or because they just don't care. But be warned: this may end up costing your organization in the long run. More and more, this is one of the biggest challenges that information technology departments face. Keep reading to learn how to mitigate this issue—or, download the IT Consolidation Checklist to get a head start on cleaning up your tech stack and increasing adoption of tools.

What is shadow IT?
Shadow IT is what happens when your employees use their own devices, software, and/or applications without an official go-ahead from your IT department.
When you’ve got employees using their personal devices at work instead of pre-approved or company-owned tech, it shows a lack of organizational structure. It’s a sign that your organization has a discipline problem and potential security risks.
Permissions protocols are there for a reason, after all. It’s difficult for your IT department to properly support the company when no one’s using the applications they’ve been trained to maintain.
How to know if shadow IT exists in your company
Aside from the most basic control measures, such as updating your BYOD policy, it can take a lot of work to reduce the occurrence of unauthorized tech in your company.
A good place to start is by looking at systems management. Who’s managing your systems, what role are they playing, and what do they use the systems for? Those are useful springboard questions to help you figure out how widespread the issue is.
From there, consider the following as simple signs that shadow IT may have crept in to your business:
Your staff is talking about unauthorized solutions. Many end users don’t realize that you can’t just install whatever you want. That means they’ll probably openly discuss using tools you haven’t okayed. So keep your eyes and ears open.
Your staff isn’t talking about authorized solutions. If you’re used to end users complaining about tools within your tech stack, those complaints suddenly stopping should be a red flag. It might be because they’ve chosen to use their own.
Your security solutions flag new threats. Shadow IT poses a significant cybersecurity risk, which we’ll get into later. If your teams are using unauthorized software or devices, therefore, your security solutions will likely start flagging new threats. Promptly investigate each new alert as they pop up.
Common examples of unauthorized SaaS applications are cloud storage service providers (like Dropbox), instant messaging apps (like Slack), softphones (like WhatsApp), and word processing software (like Google Docs). While these are not inherently risky in and of themselves (SaaS applications in general are pretty secure and many businesses use Dropbox and Google Docs), each shadow IT application is a potential blind spot in your IT team’s coverage.
How are modern IT teams thinking about their company tech stacks?
Learn more in this guide featuring 5 IT leaders' insights on building an effective tech stack.
What shadow IT is costing your company
Shadow IT brings with it two main types of costs: extra security costs and unpredictable operational costs.
Security costs
If you want your company to have excellent IT security, then you’ll want to stamp out underground software usage. Shadow IT makes it very difficult—and very costly—for companies to properly protect users from security threats. Here’s why:
Data security
Data security is one of the highest priorities of any IT organization. IT organizations need to enhance data security to protect against breaches and malicious actors like fraudsters and hackers. That’s very, very difficult to realistically achieve when your employees use unsanctioned tools.
Each device or app that has access to your company’s sensitive data poses a unique risk. If all your employees exclusively use company-issued laptops or smartphones and sanctioned software, then your IT department might have to review each occurrence case by case in the event an exception has to be made—like say if there’s mission-critical software that simply can’t be blocked because it would negatively affect the user’s project.
Alongside issues of data security, shadow IT can also create issues of data integrity and quality.
Say, for example, that the company contact center is required to use a specific program to measure call analytics and other contact center metrics. But one contact center in a different location decides to use their own program, which either measures different metrics or measures the same metrics by a different standard.
What happens to their data? At best, it just looks wrong when upper management reviews the numbers. At worst, it’s incompatible with the data collected by the rest of the organization, which makes it impossible to generate definitive and accurate insights or conclusions. It introduces inefficiencies into your process that may have long-term implications.
Compliance costs
Every company that deals with data has to make sure that they’re compliant with data regulations relevant to their industry.
One popular compliance requirement is HIPAA, which is huge for any healthcare practice or organization. Other standards can also apply depending on which sector your business is in and which territories in which you operate—companies serving EU-based customers need to be GDPR-compliant, for example.
Unfortunately, compliance doesn’t always come cheaply. That’s doubly true for companies where shadow IT is prevalent.
It’s a lot easier to guarantee that your business is fully compliant when your IT department has access to all devices and apps that are used in your company.
But when your IT employees can’t realistically check every individual device or program, it can be tough to secure compliance. That means you once again have to make a choice between opening yourself up to risks, or expending lots of extra resources on IT solutions that are basically workarounds.
💡 An example:
Learn more about Dialpad’s security and compliance measures, which are in place for its AI-powered collaboration and customer engagement solutions.
Cybersecurity threats
Security costs come down to a lot more than just ensuring data security and regulatory compliance. Cybersecurity threats in particular are a huge concern, and one that’s especially difficult for organizations whose employees use unauthorized devices and programs.
Your IT department can set up things like company firewalls that keep cyber threats at bay. However, unsanctioned devices can’t always be protected by company firewalls, security programs, or other safety protocols. This makes their vulnerabilities more apparent—gaps in your IT infrastructure that could expose you to data breaches.
There are two possible outcomes. Either your company leaves its IT infrastructure without adequate security and protection—or you expend lots of extra IT resources trying to protect against security risks that shouldn’t even be there in the first place.
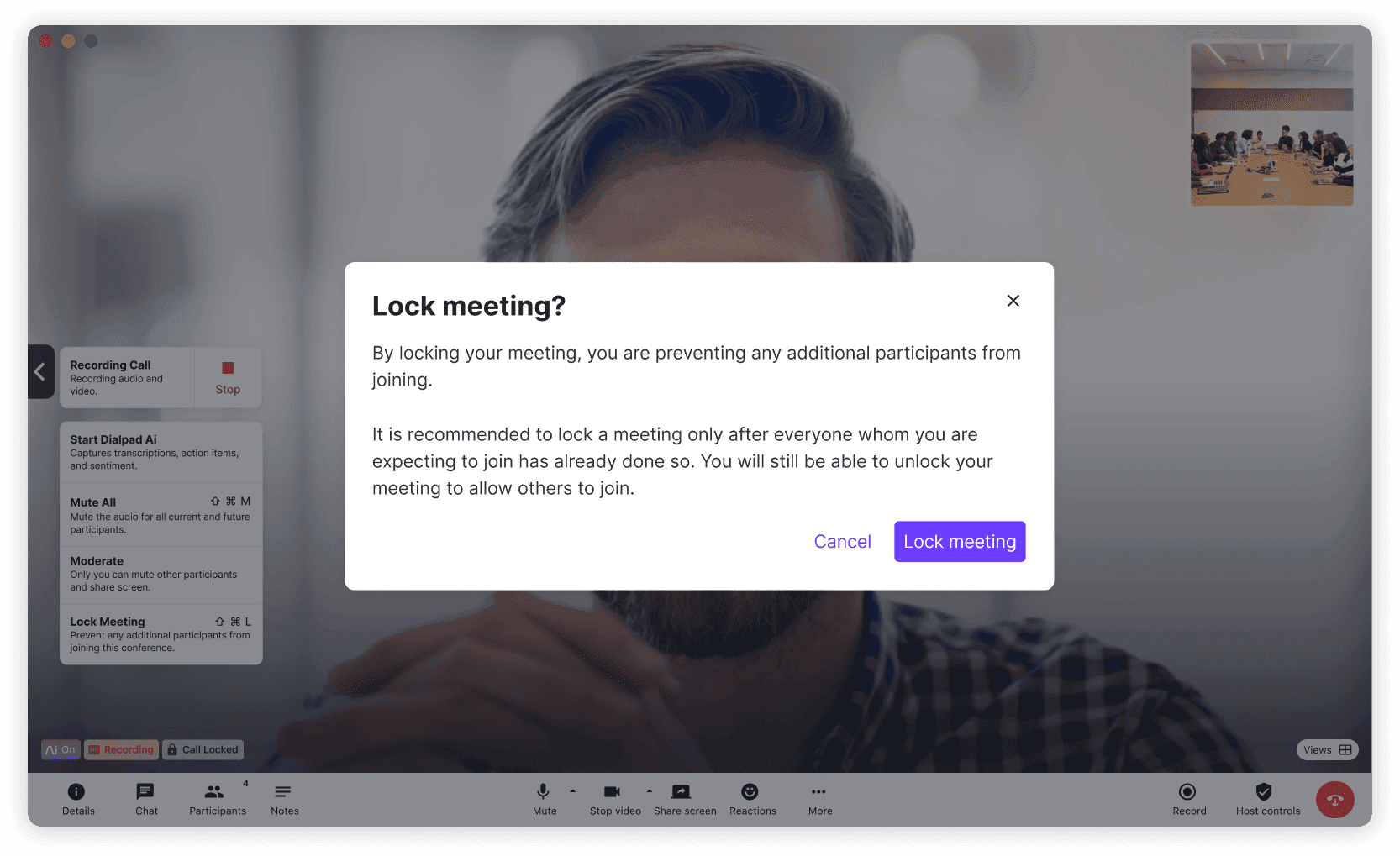
Even employees who follow cloud security best practices can be put at risk if the apps they’re using don’t come with built-in security functionality. That’s why all versions of Dialpad’s software feature built-in enterprise-level security and features like the ability to lock and unlock meetings, remove attendees, and more:
Operational costs
Shadow IT can become costly to the very process of running your business. These operational costs tend to come in three main forms:
Unauthorized software and app purchases
Unauthorized apps don’t just make it difficult for tech support, they can also have a real impact on your bottom line. That’s because applications are being purchased without regard for what’s already in the stack, straining the company budget and often meaning you’re paying for multiple tools doing the same jobs.
Lack of integration with other systems
It’s tough to design integrated systems where you don’t know what people are going to try to integrate.
Your systems are crafted to support the tech your company plans to use. Employees going off-plan can derail your systems and ironically, make it tougher for themselves to work.
Say, for example, that a sales rep doesn’t want to use the company's sales call center software, and instead uses their own third-party sales app. The approved platform is already integrated with Salesforce and other systems, but the third-party unauthorized app is not.
The sales manager now has no visibility into the rep's activities, because they're not being automatically logged in Salesforce. It's bad for the manager, and in the end, also makes more work for the rep because they'll now have to manually log their calls and activities to Salesforce.
What’s more, the implementation of any new technologies or solutions can also be negatively impacted. When end users are using their own apps and devices, it’s nearly impossible for the IT department to roll out new tech consistently across the board. Those that are already using the unauthorized apps will resist, unwilling to lose the tools they feel are already doing a good enough job.
Only good for short-term solutions
It might seem like a great idea to let employees download any apps they want when you have no time to deal with the problem. It solves any issues they’re facing at that moment.
But when months pass and suddenly every team is on a different tech stack, lots of problems will arise. Teams are working in silos, crucial data isn’t readily available to everyone, and new hires will have no idea how things are supposed to actually work.
Shadow IT creates short-term solutions that don’t address the root of why issues are coming up in the first place. It’s not suitable for long-term planning, and actively gets in the way of viable long-term solutions.
4 tips for reducing shadow IT
Tackling the root of these problems will help reduce the use of unauthorized apps or devices.
1. Determine your unmet needs
No one wakes up and chooses to break IT policy—they’re generally driven to find their own apps or solutions out of necessity.
The solution, then, is to understand the conditions that create that necessity.
Figure out where your employees aren’t having their needs met by your IT-sanctioned solutions. In the case of cloud services, it may be that a certain company-approved SaaS product lacks certain key features.
Talk to each department and ask them how their current tech stack is helping them do their job, and how they think it can be improved. Have them propose solutions that can solve the unmet needs, whether it’s upgrades to their current software or other suggestions for a new software platform.
2. Get buy-in from your business leaders
Once you’ve figured out exactly which sorts of tools, solutions, and services your teams need, it’s time to get management approval. They hold the purse strings, and you’ll need to convince them that your proposal is worth doing.
Sit down with your business leaders and get them fully on board. You’ll need to make the decision-makers understand the inherent value in giving individual teams the tools they need up front, instead of forcing them to find their own.
As with any prospective investment, leadership may initially be scared off by the dollar amounts. That means you need to convince them that the ROI will be worth the expense. Explain the benefits of altering the tech stack in terms of productivity, efficiency, security, and team morale.
3. Include relevant stakeholders in the tool acquisition process
As important as your business leaders are to your overall IT strategy, they shouldn’t be the only people involved in tool acquisition.
To ensure you choose the right tools to provide your teams what they need, you must involve those who the tools are for. Get end users from the teams who’ll be using the solutions involved in your discussions.
It’s those individuals, after all, who’ll have the best idea of the exact features and functions that they and their colleagues can’t do without. Making sure those things are covered as a minimum will ensure no one goes running to an unsanctioned tool down the road.
4. Invest in an all-in-one solution
An all-in-one solution that covers multiple requirements can be a highly effective countermeasure against shadow IT. If your teams have everything they need in one place, why would they bother downloading unsanctioned apps and tools?
For example, instead of getting a separate messaging app, video conferencing app, and conference calling app, why not get a tool that can do all of that at once? Dialpad, for example, lets you do voice calls, video conferencing, messaging and much more, all from one intuitive interface:
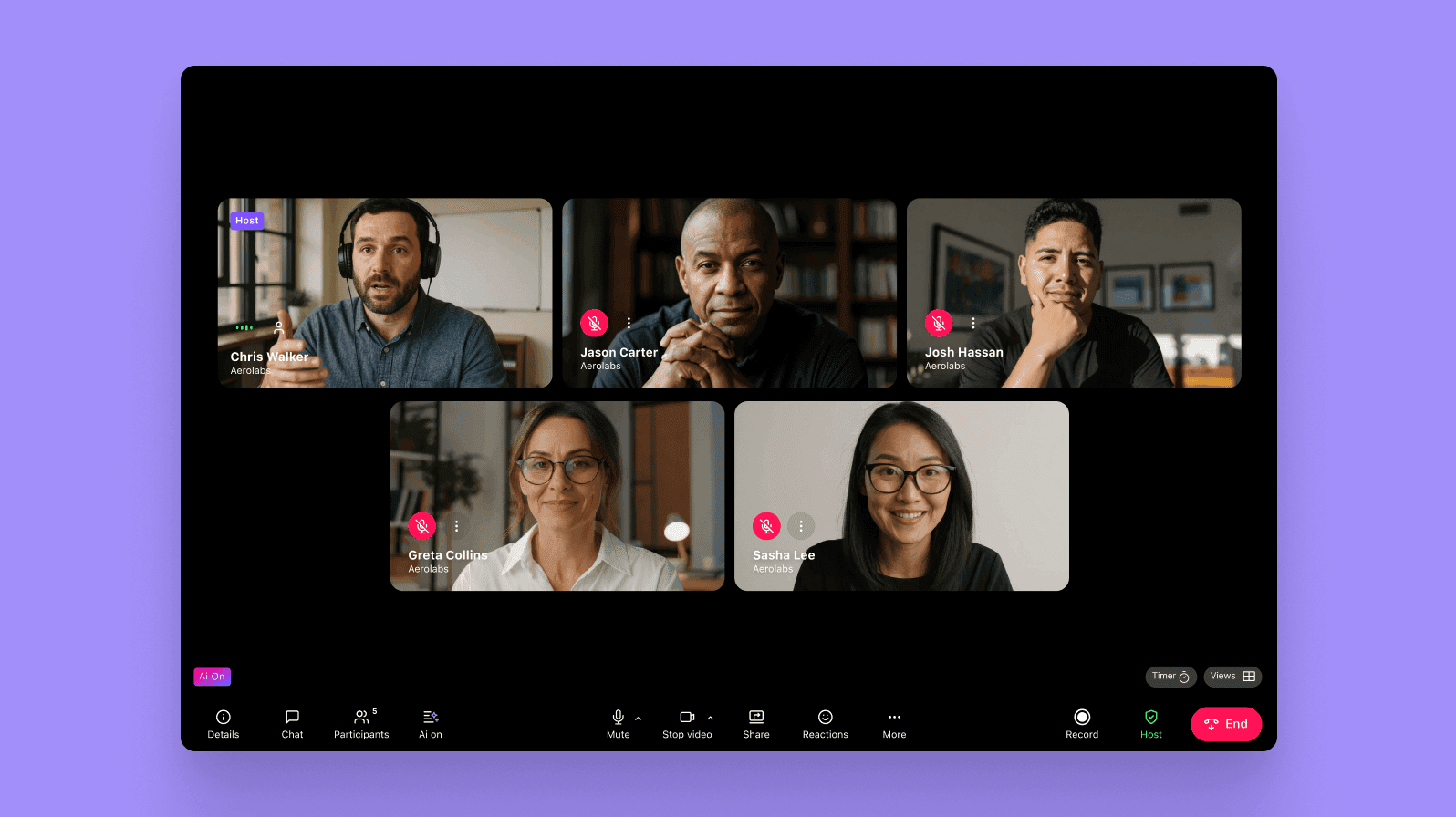
What’s more, with a huge library of integrations with collaborative platforms like Google Workspace (including Google Drive, Gmail, and Google Calendar) and Microsoft Teams as well as built-in call analytics tools, Dialpad can bring all your communications and customer intelligence functions and processes under one umbrella.
Implement intuitive, easy-to-use solutions so your company won’t lean on shadow IT
So, how can you set your company up to prevent unauthorized software, apps and devices? What you need are the right solutions that give your teams everything they need.
When your teams’ needs are effectively met by the software and hardware solutions your IT team provides, they won’t have to resort to unauthorized alternatives. Whether it’s Dialpad as a holistic customer intelligence platform or another solution that suits your business’s unique needs, building the right tech stack for your staff is your best defense against the security risks resulting from shadow IT.
See how Dialpad has helped companies avoid shadow IT
Need to consolidate communications and customer intelligence functionality, like video conferencing, phone calls, analytics, and contact center features into one beautiful platform? See how Dialpad is designed to help you do exactly this. Book a demo, or take a self-guided interactive tour of the app first!
