VoIP security and why you should be checking for these 11 risks

Manager, Network Engineering

Share
The business benefits of VoIP (aka. Voice over Internet Protocol or Voice over IP) are well known—but perhaps not so well known is the associated impact of VoIP security.
VoIP services do come with certain security risks, though these can be mitigated effectively if you’re with a good provider, so it makes sense to conduct rigorous checks to ensure that your business’ data is kept safe from cybercrime.
In this guide, I’ll walk you through 11 core VoIP risks, followed by the VoIP security best practices that, in my experience, can keep your business’ and customers’ data secure.
What is VoIP security?
VoIP security is different from traditional security systems for legacy PBX (Private Branch Exchange) or other on-premises systems in that VoIP network security is cloud-based and exists virtually. This is one of the biggest differences between a VoIP-based and legacy phone system.
A VoIP phone call is initiated via Session Initiation Protocol (SIP), which allows voice calls and messages to be sent over internet networks. It’s a commonly non-encrypted, text-based protocol that includes information about the caller’s device and the nature of the call, which is forwarded to the receiving device. Because all this data is plain text that travels across the open internet, it is open to security risks.
A more secure alternative to this is the use of an encrypted connection using Transport Layer Security or TLS. (Such as in the case of Dialpad’s enterprise VoIP service!)
This means that if the call is intercepted, the contents (including in-transit web requests) are encrypted instead of being easily understood text-based data. To ensure VoIP phone security, you can also run secure SIP calls through a virtual private network (VPN)—we’ll take a closer look at this later.
👉 Dialpad tip:
Ensure that your VPN provider gives your business enough bandwidth to facilitate quality calls and communications while ensuring VoIP security.
How VoIP security is separate from telephony security, and which web security fundamentals overlap
VoIP security protocols, which include special VoIP encryption methods, prevent possible threats such as viruses and Denial of Service (DoS) attacks. Getting a better understanding of where these protocols are deployed and how they work will ensure you’ve got your VoIP security monitoring covered.
Traditional landline phones initiate calls via the Public Switched Telephone Network (PSTN), transferring data in an analog format. Because a physical connection exists between the caller and recipient, physical protection systems have to be implemented to prevent wiretapping scenarios. These methods are difficult to implement due to certain restrictions and hefty costs.
Interestingly, businesses that are further along in their cloud modernization strategy contained data breaches on average 77 days faster than those in the early stage of their modernization journey. So, even though there might still be work to do with your security systems, if your business has embraced cloud-based communications, you’re actually better protected than organizations that use legacy systems.
Regardless of whether your business communications take place via PSTN or through secure VoIP encryption protocols, everyone at your company has to be aware of keeping customer and business data secure by handling information with integrity, and only making it accessible and available when it's required.
Which systems are already put in place for you? Where does the user’s responsibility lie?
As an example, Dialpad's communications platform protects your business’s conversations at every step with built-in enterprise-grade security. Every encrypted VoIP call you make uses WebRTC technology and Secure Real-Time Transport Protocol (SRTP) for authentication and encryption. Sensitive information like caller names, usernames, and phone numbers are encrypted with TLS protocols.
Reliable hosted VoIP providers use Session Border Controllers (SBCs) to maintain security and ensure call quality is unaffected. Your VoIP provider should handle security patches for cyberattack vulnerabilities and firmware updates.
So, what do you need to do to achieve optimal VoIP security?
First, your business could implement a VPN. VoIP over a VPN protects the SIP and your data transmitted over the internet, and maximizes your protection against hackers. A VPN is a secure and private connection between your devices and the endpoints of communications, and it keeps your business’s data safe by masking IP addresses and encrypting your VoIP traffic.
👉 Dialpad tip:
If you use a robust and secure communications provider that encrypts these requests via TLS and all other web requests via HTTPs (like Dialpad), then a VPN might not be necessary.
Your business has a responsibility to secure the implementation of all the cloud services your company handles. The onus is on your company to ensure that the appropriate security is in place to close the gap between your business’s data and the VoIP provider.
What exactly is VoIP encryption? How does it work?
VoIP encryption is the process of encrypting voice data packets during transit, thus rendering them unreadable and impenetrable by attackers.
Let’s look at this in more detail: When voice data packets transfer from the sender to the recipient, the IP protocol SRTP is deployed. We’ve covered SRTP briefly, but this protocol does three things during voice packet transfer:
Applies Advanced Encryption Standard (AES) to the data
Provides message authentication
Delivers extra security against replay cyberattacks
Market-leading encrypted VoIP providers offer both AES and TLS protocols to secure your business from cybercrime.
11 VoIP security risks and how to prevent them
Data breaches are no joke. The costs associated with data breaches rose from $3.86 million in 2020 to $4.24 million in 2021, which is the highest average total cost in 17 years.
Below are 11 of the most common cyberattack methods used to compromise VoIP security. Understanding these is the first step towards keeping your business’s VoIP system safe from security vulnerabilities.
I’ve broken this list down into two categories—the first group refers to VoIP security risks to be aware of as you’re shopping for a VoIP provider, and the second group is what VoIP providers should be aware of as they’re building out their solution.
Group 1: VoIP security risks that businesses should know when vetting VoIP providers
1. S.P.I.T.
S.P.I.T stands for Spam over IP Telephony, and is similar in nature to phishing attempts. It uses pre-recorded messages sent through your VoIP phone system to block your phone numbers. These spam messages often contain malware or viruses.
How to prevent S.P.I.T.
Implementing a solid firewall to detect spam and block it will control these types of messages and keep your VoIP system running as it should.
Dialpad offers call blocking and spam prevention features to every VoIP system user, alongside spam recognition and capabilities to block callers with high spam scores.
🔎 Case study:
See how WeWork uses Dialpad to prevent spam calls.
2. Malware
As an internet-based technology, VoIP systems are susceptible to malware and viruses that infiltrate networks. The security issues caused by malware include severe consumption of bandwidth, leading to signal congestion, and, ultimately, a breakdown in your business’s VoIP calls.
Malware attacks also corrupt data in transit, which means packet loss. But that’s not all. Malware and viruses create Trojan backdoors which leave security gaps in your data networks for future cyber criminals to exploit. These methods make it easy for hackers to steal your business’s information relayed through VoIP phone calls.
How to prevent malware
Using secure encryption methods and carrying out regular network infection checks is how to prevent malware and virus attacks on your VoIP system.
Combine that with hardware firewalls to scan information and verify its security, along with anti-virus software and strong passwords. Encourage your employees to never reuse passwords and to create passwords with capital letters, numbers, and special characters for maximum protection.
Anti-virus software works to prevent, detect, and remove malware from your VoIP system before damage occurs. It’s essential that you install anti-virus software on all devices across your business.
3. Vishing
We’ll cover both vishing and phishing here, but vishing (the voice version of phishing) is most relevant in VoIP communications.
Email phishing targets businesses and encourages them to provide information by clicking on an unauthorized link. VoIP systems are subject to the same schemes, but instead of an email subject line, cyber criminals infiltrate the caller ID. For example, vishing hackers often try masquerading as banks to obtain user data.
How to prevent vishing
To prevent a vishing attack on your company, never provide information over the phone to anyone claiming to be from the IRS or Social Security Administration, as these organizations do not initiate contact. It’s a good idea to join the Do Not Call Registry to protect your business’s inbound number.
In addition to these measures, implement Multi-Factor Authentication (MFA) which requires users to verify their identities before accessing a system that could be compromised. This makes it far less likely for cybercriminals to steal your personally identifiable information.
👉 Dialpad tip:
MFA applies not only to your business’s phones, but also to your workplace apps and all parts of your VoIP service. We’d recommend integrating your business systems with a Single-Sign on Provider that enables strong MFA.
Train all employees so they know how to detect vishing attempts by educating them about common signs such as:
Unexpected phone calls from well-known businesses or numbers
Sudden urgency from the caller to provide sensitive information
Unusual or short phone numbers on the call screening display
Voice prompts via touch tones or voice answers
The caller repeatedly requests verification of information
4. Service theft
Service theft (also known as toll fraud) happens when hackers intercept your VoIP system with the intention of using it for their own purposes. In this situation, your business is left with an extortionate bill. Commonly, service theft criminals dial international and premium rate numbers and are able to steal your business’s information at the same time.
How to prevent service theft
Prevent a service theft attack by firstly ensuring that your encryption methods are robust. It’s essential that your network is as secure as possible, and your employees must use secure credentials.
Consider increasing your network’s password strength requirements for maximum protection against VoIP service theft, and keep your VoIP network on a separate network from your regular network to ensure that attackers can’t leverage one to jump to another.
5. Packet sniffing
Packet sniffing security attacks allow hackers to log unencrypted data in data packets while in transit. This can result in packet loss and cause slow service (known as a black hole attack), but it can also be a completely silent attack. During a packet sniffing attack, hackers can also inject packets into data streams and intercept your business’s network traffic, causing either slower or a complete loss of network connection.
Data that is liable to be stolen includes passwords, usernames, and other sensitive information. Criminals seek login data from personal messages and emails to help them steal personal data.
There are two types of packet sniffing attacks:
Active—Hackers target a specific network device to capture the traffic between two endpoints. An active attack is usually used for targets of high-value.
Passive—Hackers infiltrate a hub connected to other devices via a LAN. Any information or data is up for grabs in a passive packet sniffing attack.
How to prevent packet sniffing
The best way to prevent packet sniffing is to invest in a robust VoIP VPN which ensures that your data and all information is secure. Avoid using public Wi-Fi, as it’s easy for cyber criminals to sniff a public Wi-Fi network and steal the data.
👉 Dialpad tip:
When you're browsing websites, make sure their URLs start with HTTPS for maximum security.
6. Spoofing
Spoofing is a malicious cyberattack used to trick people into picking up calls by emulating the caller ID to display a local, or less suspicious, phone number. Typical call spoofing goals include obtaining sensitive personal information.
How to prevent spoofing
The only way to protect your business from phone spoofing is by mitigating the problem, as you cannot stop spoofing instances altogether. Train your employees to be aware of the risk of call spoofing and how to spot it.
Group 2: VoIP security risks that VoIP providers should be aware of
7. Call tampering
The next VoIP security threat on the agenda is call tampering.
Call tampering is when a cybercriminal destroys the quality of business phone calls by introducing noise packets into the call streams. Although less severe than some of the VoIP security threats we’ll cover, call tampering often forces both callers to end their call and sometimes prevents data packets from being transferred to their intended destination. This results in problems such as long silences and intermittent reception on the line.
How to prevent call tampering
Ensure that your business’s VoIP service has TLS encryption to authenticate data packets, along with encryption and endpoint detection software.
8. Denial of service (DoS)
DoS attacks occur when cybercriminals flood your network with traffic so that authorized communications are blocked. Typically, these types of attacks are caused by remotely-controlled computers or bots manipulated by hackers. As a result, call center operations can experience lower call quality, less uptime, and latency.
👉 Fun fact:
Dialpad uniquely provides 100% uptime for Enterprise plan customers—the current industry gold standard is 99.999%. Our multi-tenant architecture, geo-located redundancy, and rolling deployments ensure that our Enterprise customers remain connected 24/7.
Other businesses may notice signs of DoS attacks, such as:
A sudden traffic surge from IP addresses and locations from matching devices
503 HTTP error responses
Unexpected and persistent spikes in bandwidth
How to prevent denial of service
Mitigating DoS attacks requires a separate VoIP internet connection. Using a dedicated Virtual Local Area Network (VLAN) for VoIP traffic is a solid choice. Implementing VLAN makes it simpler to recognize unauthorized traffic and spot a DoS attack sooner.
Opting for managed encryption services, especially in the context of SD-WAN, is the best route for businesses that have users sharing data across Wide Area Network locations (WAN).
9. Man-in-the-middle attacks
Man-in-the-middle attacks occur when a hacker gets in between your VoIP network and the call’s recipient.
Public and unsecured Wi-Fi networks are prone to man-in-the-middle attacks, which result in hackers intercepting phone calls and re-routing them through their own servers. During this time, hackers can infect calls with malware, viruses, and spyware.
How to prevent man-in-the-middle attacks
Avoiding public and unsecured Wi-Fi networks can help with this type of cyberattack, but with the rise of the “work from anywhere” movement, this is not always possible—or realistic. One recommendation is to have your employees use a virtual private network (VPN) when they’re using devices in a public area. If you’re managing a Wi-Fi point, checking that your router login credentials are secure and implementing robust WAP/WEP encryption on access points are also ways to tighten VoIP security.
If you’re using public networks, make sure that your VoIP services provide encryption through the entire lifecycle of a phone call.
10. Toll fraud
Toll fraud is when hackers make an excessive number of international calls from your business phone system. The purpose behind toll fraud is for cybercriminals to obtain some of the revenue that these calls generate.
Toll fraud is also known as International Revenue Sharing Fraud (IRSF), and involves Premium Rate Numbers (PRNs). Classified as the most persistent type of fraud within the telecom industry, it’s also challenging to eliminate due to its many moving parts (mobile network systems and multiple operators).
How to prevent toll fraud
Use a script breaker like CAPTCHA.
Implement two-factor authentication on your accounts.
Set rate limits on call durations and concurrent phone calls.
Restrict geo-permissions.
11. V.O.M.I.T. attacks
The delightful acronym V.O.M.I.T (Voice over Misconfigured Internet Telephones) is a type of cyberattack that converts conversations into files.
During these attacks, hackers can steal information located in these converted files as they can be played in any location.They can obtain all sorts of sensitive information about your business, including usernames, passwords, bank information, and phone numbers.
How to prevent V.O.M.I.T. attacks
Using a cloud-based VoIP provider that offers robust encryption secures calls before they’re initiated. Healthcare businesses that must prove compliance with HIPAA need a solid fixed VoIP system that is more secure than a public network.
6 best practices for securing your VoIP security system
When it comes to your VoIP phone system or contact center software, you can’t just tell your employees to set a strong password for their Wi-Fi networks and call it a day. Regardless of device or network (IP phone, softphone, desk phone, or smartphone), a security threat could still be on the horizon.
Here are some recommended VoIP security best practices to adhere to:
1. Audio fencing
Audio fencing is a phone system feature that eliminates background noise to keep calls quiet in busy areas such as call centers. Using this feature is considered best practice for securing your VoIP system due to the virtual “fence” environment it creates—ensuring that calls can’t be overheard and sensitive details relayed accidentally.
2. Encourage employees to update software / operating systems often
Adhering to the security best practice of updating operating systems and software reduces the chances of malicious software infiltrations.
Encourage your team members to accept OS updates for their mobile devices and always use the latest version of your business communication tools. Remember that operating system updates contain essential security updates and protect your VoIP system against unknown malware and viruses.
💡 What about VPNs?
VPNs are a hot topic, but today, many businesses don’t actually need or use VPNs because for SaaS applications, it’s no longer a necessary layer. Only when traffic is going over https or packet metadata is sensitive (rarely the case these days) would using a VPN be necessary. Instead, ensure that you manage your accounts well and that your SSO systems are connected to your VoIP provider with the utmost security (such as strong passwords and MFA). Monitor your accounts regularly for unexpected behavior.
3. Make sure you can block spam calls
Look for a trusted VoIP provider like Dialpad that has built-in spam recognition features. Using an automatic spam blocking system and user-level settings, you can control how calls to your Dialpad number are handled.
Set up customized filters to mark specific numbers as spam and block all communications for peace of mind.
With Dialpad, you can choose how you want to handle certain calls in different ways, including “send to voicemail” and “send directly to spam folder without notifications."
4. Delete inactive employee accounts
As soon as employees leave your business, it’s a good security practice to deactivate their user accounts.
Inactive accounts are easy ways for hackers to infiltrate your network and get access to your VoIP system. Make sure your employees know to notify the IT team of employee departures quickly so you can delete inactive VoIP accounts and reduce business disruptions.
5. Set up remote device management
Implement a scheme for employee remote device management. This security measure ensures that your business is able to wipe a device during a security breach and contain any cyber threats.
Similar to deleting inactive accounts, setting up remote device management enables your IT department to quickly take control of devices in security situations.
6. Choose a secure VoIP provider
How secure your VoIP system is ultimately lies with your VoIP provider and the level of security provided. Business security needs will vary. For example, your industry may be subject to PCI compliance regulations. To choose a secure affordable VoIP provider, create a list of VoIP security based questions:
How long does it take to respond to security breaches, and how long to restore safe service?
Do you offer TLS and SRTP encryption protocols?
Do your encryption protocols impact call quality?
How do you physically protect your servers?
What additional measures are in place to mitigate phishing, toll fraud, and DNS attacks?
How do you train staff?
What accreditations have you received?
Do you use third-party tools, and if so, how do you ensure that they are following security protocols?
What kind of customer support is available?
Before choosing a VoIP provider, check your business’s VoIP requirements. Here are some examples of industry compliance accreditations:
Health Insurance Portability and Accountability Act (HIPAA)—This act decrees that healthcare service providers have a responsibility to secure patient data, and applies to phone systems and their features, such as call recordings and voicemail functions.To comply with HIPAA, relevant organizations’ servers must be configured to protect patient privacy. Healthcare providers are common targets of cyber attacks due to criminals trying to access patient records to perform identity theft.
Cloud Security Alliance (CSA)—The CSA Code of Conduct for GDPR compliance that documents security controls in IaaS, PaaS, and SaaS services.
ISO/IEC 20071 standards—The global standard that addresses businesses’ responses to security threats. Gaining this accreditation means that you have implemented stringent information security controls.
Service Organization Control (SOC 2)—Compliance practices that ensure consumer trust across elements of privacy, security, data integrity, and availability. It’s common for cloud-based SaaS businesses to meet SOC 2 compliance. Achieving SOC 2 certification validates adherence to stringent security and privacy standards.Compare your potential VoIP provider’s accreditations with your business’s requirements to assess the best service fit and ensure compliance.
👉 Fun fact:
Dialpad is SOC 2 compliant through a third-party audit and offers HIPAA-ready products. In addition to these accreditations, Dialpad is a member of the CSA and its infrastructure and processes are annually certified against ISO 27001:2022, ISO 27017:2015, and ISO 27018:2019.
Features to look for in a secure, encrypted VoIP service provider
When you’re looking for a VoIP solution, VoIP security should be at the top of your features list. Whether you’re running a small business or a large enterprise, take the time to do your due diligence on the VoIP system that you’re considering implementing. This includes:
Asking VoIP providers detailed questions about their VoIP cyber security protocols.
Reviewing the VoIP providers’ most recent audit report.
Checking the guaranteed uptime—strive for 99.999% at a minimum.
Let’s take a look at other important features of a VoIP phone system to ensure you're choosing the most secure IP telephony solution for your business.
Secure call recordings
Businesses use call recordings for a variety of reasons—from onboarding training and improving agent service, through to monitoring verbal contracts. Dialpad customers have peace of mind that all recordings’ data at rest is encrypted with AES 128-bit ciphers, with encryption keys managed using Google’s encryption management and 90-day key rotations.
Dialpad also allows admins to configure call recording settings to comply with applicable laws. It lets you play automated prompts to alert callers, and has in-call indicators as well to be transparent about recording times. AI-powered granular controls can also pause recordings automatically whenever sensitive data, such as payment information, is detected on screen.
When you’re sharing your recordings or transcripts for training purposes, your customer service agents can feel secure that they aren't sharing information they shouldn't. When someone wants to share a link, Dialpad automatically detects if the conversation contains a credit card number or other potentially sensitive number (like a social security number):
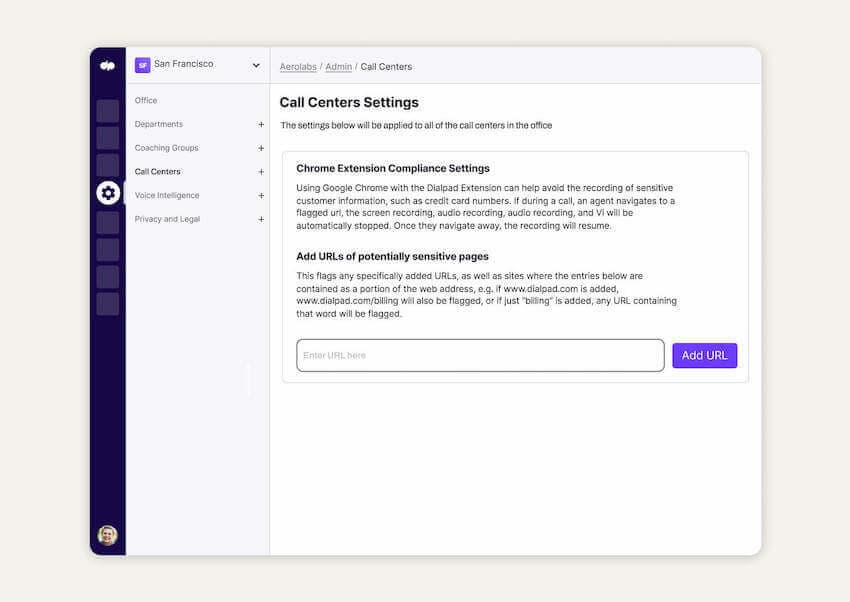
Another useful feature in your VoIP toolkit is an “exception list”. An exception list allows you to add area codes that should automatically be excluded from recording. Build your business’s exception list to navigate all-party consent states or GDPR regulations.
Alternatively, when sensitive information crops up during phone calls, your agents can also just use Dialpad’s manual pausing feature.
Call encryption
Seek a provider like Dialpad that uses measures like TLS and SRTP to encrypt phone calls and provide complete privacy and data integrity. Voice packets are encoded in SRTP (Secure Real-Time Protocol) as soon as calls begin and someone starts speaking. It ensures encryption, integrity, message authentication, and replay protection.
In these instances, VoIP calls conducted via Dialpad are more secure and safer than phone calls over a traditional phone network—without compromising call quality.
VPN connection
Virtual Private Networks (VPNs) encrypt all voice traffic, regardless of location, so it’s perfect for remote teams.
A VPN connection is especially important when HTTPS is unavailable and employees are away from the secure office network. A business-grade VPN ensures that call quality is unaffected.
Industry compliance across the board
An audit report is a good indication that the VoIP provider takes their security compliance seriously, so you can be confident that their VoIP infrastructure is solid. VoIP encryption isn’t a “nice-to-have”, it’s a “must-have”. Seek business VoIP plans with services that support the aforementioned TLS or SRTP encryption protocols as a basic standard without paying any extra.
Customizable data retention and management policy
The most secure VoIP providers offer customizable data retention policies. The three main types of customizable data retention options are:
Customizable durations
Based on specific department or contact centers
Based on data type
Different industries may have specific requirements around data retention, so ensure that your software has options that suit your business’s specific needs. Dialpad offers additional helpful compliance features in the form of voice transcriptions to unlock meaningful insights from your customer conversations. This works by making your voice data searchable and quantifiable.
Dialpad retains your business’s data securely until you choose to delete it, and transient data through Dialpad’s data centers is held for no more than 72 hours. Dialpad Enterprise customers can set their own retention policies to remove, archive, or anonymize data on a custom time interval.
👉Dialpad tip:
Ask about Dialpad’s API and Chrome extension option for automatic pausing of both recordings andvoice transcriptions.
Single sign-on
A single sign-on (SSO) VoIP feature provides secure auto login to all your business’s apps on-premises or in the cloud. This rapidly increases the security of your VoIP services.
The advantages of using SSO include:
• Improving security by eliminating users noting down passwords in an insecure way.
• Reducing user time spent re-entering passwords.
• Lower IT costs due to fewer number of password-related IT calls.
• Enhancing customer satisfaction with increased first call resolution rates.
• Eliminating misuse of unattended telephones.
Role-based access
Role-based access helps you control access to certain features, and can be configured at company, department, office, or user level.
Try to find a VoIP provider like Dialpad that has a security system that delivers authorization mechanisms and native authentication to ensure permissions and data are accessed through verified protocols such as OAuth.
If your business doesn’t need certain features, it’s generally a good practice to turn them off to avoid accidental use or security breaches. For example, if you’ll never need international calling, make this feature unavailable to all users.
👉Dialpad tip:
With Dialpad, you can even opt to assign granular permission levels for platform-wide integrations with encrypted VoIP app features.
Need a secure VoIP platform?
A secure VoIP platform will offer your business the best-in-class certifications and robust protocols for encrypted VoIP calls for a secure calling environment.
A provider that delivers comprehensive VoIP troubleshooting documentation like Dialpad is one that will always be on hand to answer your VoIP security questions and provide confidence in the service.
The more robust your VoIP platform, the more successfully your business can eliminate potential security threats—threats that can potentially cost your company valuable time and money.
Get a firsthand look at Dialpad's VoIP security features
Book a personal walkthrough of the platform with our team! Or, take a self-guided interactive tour of the app to play with it on your own first.
