Contact center security: 5 best practices for protecting customer data

Senior Account Executive, Contact Center

Tags
Share
With more and more contact centers adopting a remote work or hybrid work model, call center security is now more important than ever.
The good news is that there are different ways to tackle this, between adopting Bring Your Own Device or BYOD policies, and basic VoIP security best practices.
Having worked in the contact center space for many years, with customers across a wide range of regulated industries like healthcare and law, I’ve been a part of a ton of migrations to cloud platforms. In this guide, I’ll share some of those insights when it comes to call center security strategies. Keep reading to learn more.
The importance of call center security
Every data breach is costly to your business. One study by IBM suggests that the average cost of a data breach is $3.92 million, and that number is on the rise. In the finance side, credit сard data breach statistics show that the financial sector is particularly vulnerable, with the potential for significant losses and damage to customer trust.
Not only that, but your contact center contains a wealth of sensitive information. Names, phone numbers, and even social security numbers reside on personal computers and corporate servers. For that reason, data breaches can pose significant security risks to your customers too.
Remote work makes contact centers more vulnerable by exposing multiple systems to the Internet and prying eyes. Luckily, there are tools you can use to reduce liability and protect your assets.
Use these best practices to keep your tech safe, and be sure to get your employees in on your security efforts too. A well-rounded strategy is even more vital in a world where employees are working remotely and IT teams are swamped with external services and network requests.
5 contact center + call center security best practices
1. Thwart attacks at login
The first barriers you put up between the web at large and your company data are the login pages for your services. With the need to access numerous systems in the modern workplace, it’s tempting for employees to reuse login information or rely on easy-to-remember and equally easy-to-hack passwords. Both scenarios are a problem.
Protecting applications today means offering a simplified user experience backed by powerful security mechanisms. Cloud service providers offer single sign-on supported by field-tested policies such as multi-factor authentication, SCIM, and SAML.
Single sign-on (SSO) offers many benefits to your team and data security. When properly implemented by your IT staff and cloud providers, you gain access to better threat detection, experience less password fatigue, and enjoy a more productive workforce. Okta, OneLogin, Google, and Azure can even tether each agent to their hardware by IP or MAC address.
2. Use role-based access
Isolating the resources an agent interacts with once they start using your software is another way to improve security. You would never let a new low-level employee have access to trade secrets, the corporate checkbook, or the company jet—the same holds for software and cloud resources.
More than 84% of hackers use social engineering as part of their attack strategy. Instead of exposing your technology, they reveal employee’s weaknesses to gain access to passwords. This is a difficult issue to control and was responsible for past breaches at Twitter and Verizon.
Role-based access limits the information that employees have access to based on need and job title. Granular permission levels let you gradually increase employee access based on trust and their position within the company. They let you quickly remove access after a demotion or detected vulnerability. Responding swiftly to threats and giving access to only necessary resources are part of any solid security policy.
3. Use encryption
Your remote agents aren’t your only weakness. Threats are lurking between your employees and services and in your databases as well.
Spoofing and man-in-the-middle attacks let hackers snoop on data passing through your intranet or over the Internet. If an attacker accesses your computer, they can read unencrypted files with ease.
Encryption helps stave off these threats. SSL certificates, TLS, and virtual private networks help secure information in transit from one place to another. Encryption at rest secures data on your servers or in the cloud to limit exposure in a breach. For employees using their iPhones for work apps, knowing how to use VPN on iPhone is crucial for protecting.
Never leave sensitive files and data in an unencrypted state. SaaS tools and the Google Cloud Platform are an excellent option for obscuring sensitive data. These off-the-shelf solutions are easy to install and are updated regularly.
4. Contact center threat monitoring
No system is infallible. Even SSL contains loopholes that are still being discovered. With so many avenues for attack, it can be challenging to monitor every transaction and respond quickly when a threat becomes obvious.
Remote work only makes this more difficult. Your IT team tracks more IP addresses and looser usage patterns than in the past. Although not recommended, they may even have to allow unknown IP addresses to access hardware and services.
Take intuition out of the equation with cloud services and third-party tools using artificial intelligence to find real-time threats. Google, Azure, and ElasticSearch all offer advanced threat monitoring tools, and Azure even audits your systems.
5. Maintain strong security policies
Wrapping up these strategies into a strong security policy is a must for any company. NIST provides guidelines for implementing procedures related to everything from passwords to encryption to ensure data security, whether your agents are in-office or working remotely.
If your contact center develops its own software or uses third-party providers, ensuring container security is part of the overall strategy is recommended. This helps safeguard customer data by isolating different system parts so a breach in one area doesn’t compromise the whole network.
Audit your call center every year and incorporate security into your training. Implementation and review work together to harden your call center against a data breach.
The complete call center security compliance checklist
There's a variety of different approaches to compliance. If you’re in healthcare, for instance, you’d need to maintain HIPAA compliance (no need to worry about this if you’re not in healthcare). If your contact center takes payments, you’d need PCI compliance.
For a compliance checklist I'd look for:
Call or screen recordings + retrieval
Having the opportunity to review an agent's screen can provide insights and ideas or how to improve workflows and processes. That’s one benefit.
It also helps you make sure that your agents are following procedures and collecting the right data during customer conversations. For example, if one of your customers insists that they spoke with an agent about changing the date of a reservation, you’d be able to easily verify that if you had screen recordings that showed what that agent entered into their computer when they updated the reservation date.
Another example: I recently called a hotel to book a reservation and I was told it would be $250 a night. But when I got to the hotel, they said it was $450 a night. I asked for a recording of the call, and it proved that we’d agreed on the lower rate!
With Dialpad's contact center platform, you can easily start and pause recording with just a click:
QA scorecards
If your contact center platform has QA scorecards, it can make your life much easier since you can quickly do quality assurance and see if agents are doing and saying the things they need to stay compliant on calls with customers.
Industry compliance requirements
Again, this all depends on your industry. There’s HIPAA in healthcare and FERPA for education, just to name a few—your contact center technology and agents should be equipped to handle the different requirements for these when it comes to things like call recordings and transcriptions.
With Dialpad, for instance, the built-in AI can automatically pause recordings when sensitive information is being shared, to help you stay compliant:
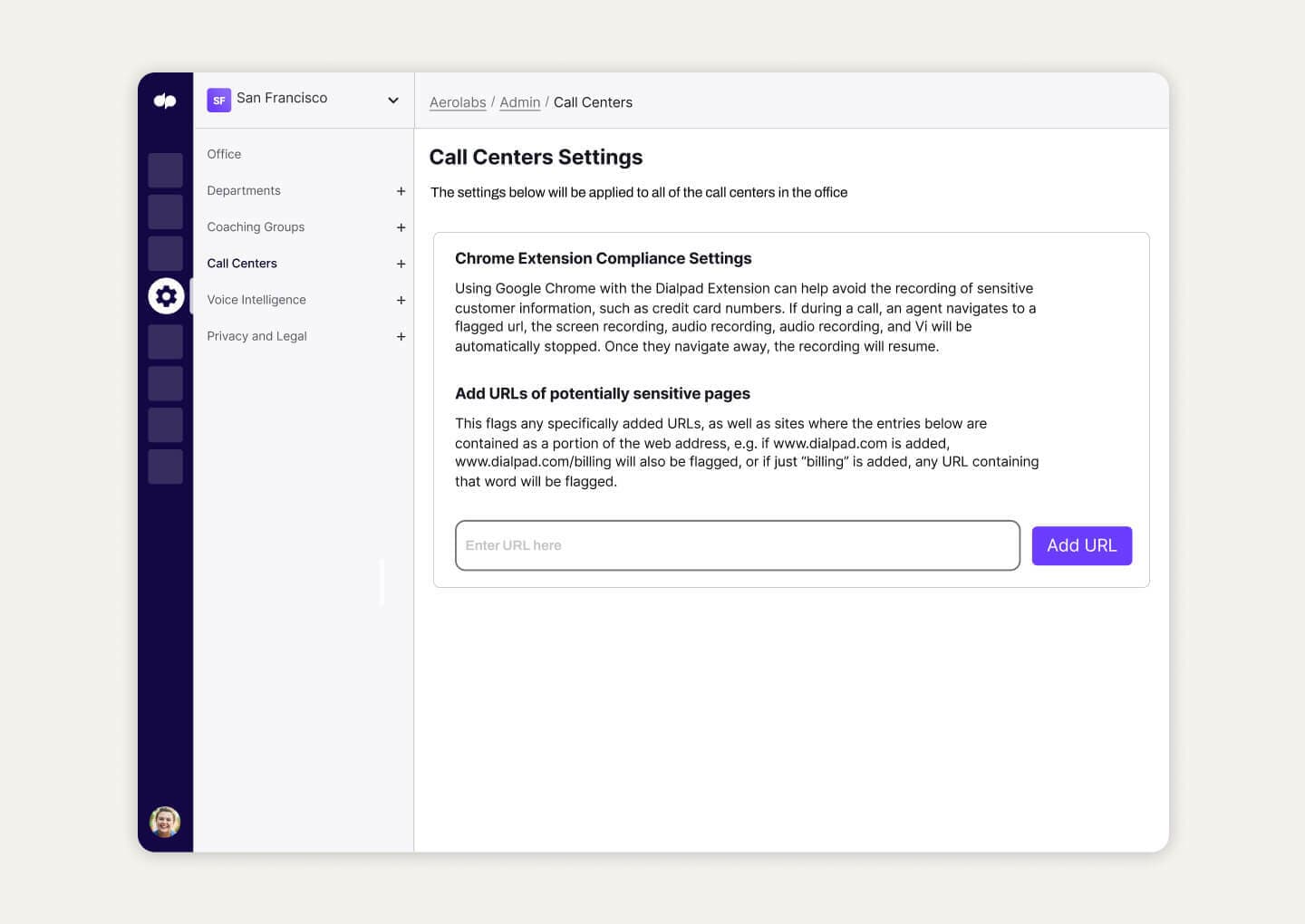
Regular agent training on proper compliance procedures and guidelines
The thing with compliance and regulations is that they rarely stay static for too long. (Medicaid’s requirements around call center recordings is a good example.) Make sure your agents are always up to date on the latest requirements.
When I worked at another company previously selling a WFO/WEM product, I had a prospect in the industry industry that was always ahead of the curve legally speaking. It was also a key time as California had just passed the CCPA, or California Consumer Protection Act.
Essentially this legislation states that any company doing business with a California resident has to have consent to record any interaction, and also keep all of those recordings and interactions readily available for a certain number of years.
So, if you called up an insurance company and told them you wanted all your past interaction data, they would have to provide it to you. For each call recording that they couldn't provide, they would be fined—in insurance, I believe it was $250,000.
What I'm getting at here is that just recording the calls isn't enough to maintain compliance. A company needs to be able to easily access and retrieve that data too—not just to protect themselves from legislation, but also in case of any one-off situations with their own customers.
🔎 A case study in call center compliance:
Let’s say there was a highly ambitious, growth-focused college that was telling prospective students things like "guaranteed job after graduation" or "free money for college." And let’s say that the government realized this was going on in the higher ed industry and passed a law to crack down on these practices. To maintain call center compliance, this college would have to be able to run a search for those phrases and make sure agents are staying compliant with how they pitch the school to students or parents.
See how Dialpad can help with call center security
From unsecured logins to storing customer data, remote work exposes multiple systems to attack. Get on top of your data security by following proper practices, securing your teams’ login portals, creating role-based permissions for remote agents, and reviewing policies regularly.
See how Dialpad’s unified platform can help with call center security now!
Learn more about Dialpad's secure contact center platform
Get a personal walkthrough with our team or, take a self-guided interactive tour of the app first!
